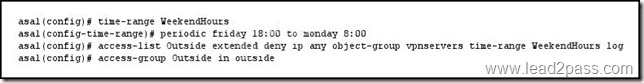
300-175 New Questions Free Download In Lead2pass:
https://www.lead2pass.com/300-175.html
QUESTION 11
Which option describes the possible result of a customer configuring a server pool that contains Cisco UCS B200 M2 and B250 M2 blades?
A. A service profile cannot migrate automatically from one blade to another blade within the server pool due
to hardware failure.
B. You must decommission a blade server for the associated service profile to migrate to another blade in the
server pool successfully.
C. You must uncheck the Restrict Migration box in the service profile to allow service profile migration between
blades in the server pool.
D. After service profile migration, the server fails in boot from SAN due to differences in PCI device IDs.
Answer: D
QUESTION 12
Which two options occur when a server discovery policy is invoked? (Choose two.)
A. executes the qualification in the server discovery policy against the server
B. applies the scrub policy to the server
C. analyzes the inventory of the server
D. assigns the server to the selected organization, if configured
E. creates a service profile for the server with the identity burned into the server at time of manufacture
Answer: AC
QUESTION 13
If a customer wants to maximize the capability of server mobility with the Cisco UCS deployment, what two options are Cisco recommended? (Choose two.)
A. Configure a server inheritance policy.
B. Configure a Virtual Media boot.
C. Configure a hardware-based service profile with burned-in addresses and identities.
D. Configure boot from SAN.
E. Configure service profiles with resource pools.
Answer: DE
QUESTION 14
You have a Cisco UCS B200 M2 server configured with 12 4-GB DDR3 1333-MHz dual-voltage memory DIMMs. You learned that the server memory speed is running at 1066 MHz instead. How can you configure the server to run at maximum memory speed?
A. You cannot configure memory speed of 1333 MHz. The maximum memory speed of a Cisco UCS B200
M2 server with 12 4-GB DIMM is 1066 MHz.
B. Memory speed of the ESX host is configurable on VMware vCenter.
C. Create a BIOS policy. In the RAS Memory BIOS settings, select Performance Mode for LV DDR Mode.
D. On the CIMC of the Cisco UCS B200 M2, select 1333 MHz in the Memory Speed option.
Answer: C
QUESTION 15
Your systems engineer has determined all of the firmware versions that the server operating system supports. What steps are taken on Cisco UCS to avoid manual firmware upgrades on the blade servers?
A. Use Cisco UCS Manager firmware management to upgrade all Cisco UCS blade servers to the same target
firmware versions.
B. Configure host firmware package and management firmware package policies and associate the firmware
policies with the service profiles.
C. Create a BIOS policy and define the host firmware package and management firmware package.
D. Configure host firmware package and management firmware package policies and associate the firmware
policies with the server pools.
Answer: B
QUESTION 16
When you create a vHBA, what will you achieve by enabling persistent binding?
A. This feature allows the binding of the SCSI targets to the vHBA, even across reboots.
B. This feature allows the binding of the same WWPN from the pool to the vHBA, even across reboots.
C. This feature allows the binding of the same WWNN from the pool to the vHBA, even across reboots.
D. This feature allows the binding of the Fibre Channel uplink to the vHBA, even across reboots.
Answer: A
QUESTION 17
Which two tasks enable jumbo frames on a Cisco UCS system? (Choose two.)
A. In the LAN cloud on Cisco UCS Manager, configure MTU 9000 in the uplink interfaces.
B. In the LAN cloud on Cisco UCS Manager, enable jumbo frames in Fabric A and Fabric B.
C. In the LAN cloud on Cisco UCS Manager, configure MTU 9000 in the VLAN.
D. In the LAN cloud on Cisco UCS Manager, define a QoS system class with MTU 9000.
E. In the service profile, configure MTU 9000 in the vNIC.
F. In the service profile, configure MTU 9000 in the virtual machine.
G. In the service profile, configure MTU 9000 in the uplink interfaces.
Answer: DE
QUESTION 18
Which three items represent some of the components to implement Cisco VM-FEX for Cisco Unified Computing System Manager B-Series blades? (Choose three.)
A. Cisco VSM VM
B. VEM installed on the VMware vCenter server
C. VEM in the VMware ESX or ESXi host
D. Cisco Unified Computing System Manager version 1.2 or higher
E. VMware vCenter server
F. Fibre Channel VMFS volume
Answer: CDE
QUESTION 19
Which three items represent some of the features that can be defined in a Cisco Unified Computing System Manager port profile? (Choose three.)
A. QoS policy
B. ACL
C. NetFlow
D. port security
E. network control policy
F. VLAN or VLANs
Answer: AEF
QUESTION 20
Which three items must be configured in the Port Profile Client in Cisco Unified Computing System Manager? (Choose three.)
A. port profile
B. DVS
C. data center
D. folder
E. VMware vCenter IP address
F. VM port group
Answer: BCD
300-175 dumps full version (PDF&VCE): https://www.lead2pass.com/300-175.html
Large amount of free 300-175 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDVDYyRldqb1AzenM
You may also need:
300-165 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDSkhBVngxX0Z3Y0k
300-170 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDdHhmcTBIbGM4bmc