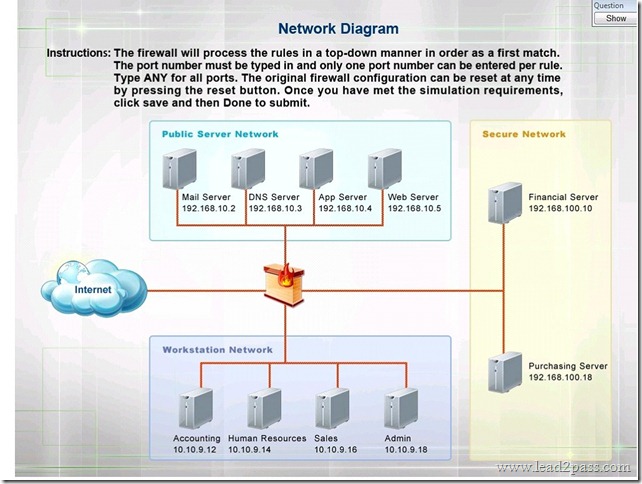
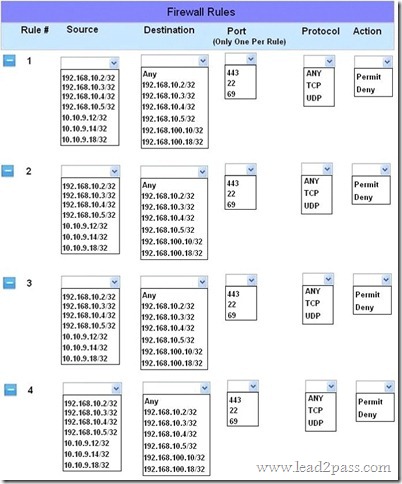
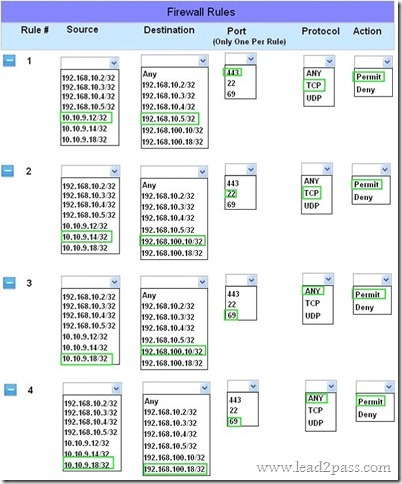
100% Pass 70-697 Exam By Training Lead2pass New VCE And PDF Dumps.v.2018-3-1.254q:
https://www.lead2pass.com/70-697.html
QUESTION 216
You administer Windows 10 Enterprise computers.
Users are able to download applications from the Internet and install them on their computers.
You need to ensure that users can install only digitally signed applications from approved publishers.
What should you do?
A. Create AppLocker Publisher rules.
B. Turn on Windows SmartScreen.
C. Enable the Check for signatures on downloaded programs option.
D. Add publishers’ websites to the Trusted Sites zone.
Answer: A
QUESTION 217
You are a desktop support technician for your company.
You deliver new Windows 10 Enterprise laptops to the software developers. The software developers frequently use laptops to work remotely and are often disconnected from the corporate network. One of the software developers works on an application that must run on Windows XP, Windows Vista, Windows 7, and Windows 10 Enterprise. The software developer needs the ability to test the application natively on each of these operating systems.
You need to provide the software developer with a way to test the application on all operating system versions on the new laptop. The software developer must be able to perform the testing while working remotely without access to corporate resources.
What should you do?
A. Use Hyper-V to create three virtual machines that provide Windows XP, Windows Vista, and Windows 7 environments.
B. Install the Windows PE version of Windows XP, Windows Vista, and Windows 7 on three USB drives and boot from each drive to test each operating system version.
C. Change the compatibility mode settings of the application to Windows XP, Windows Vista, and Windows 7 before testing each operating system version.
D. Create three virtual machines for Windows XP, Windows Vista, and Windows 7 on a company Windows Server 2012 that is running Hyper-V.
Answer: A
QUESTION 218
You support Windows 10 Enterprise desktop computers. Your company has a security policy that controls multiple settings of the desktops through the domain group policy.
The security policy recently was updated to require that access to several built-in Windows 10 Enterprise tools be prohibited to all local users on one of the desktop computers.
You need to implement this new policy.
What should you do?
A. Configure NTFS permissions.
B. Create a Windows To Go workspace.
C. Configure the AppLocker policy.
D. Enable BitLocker.
Answer: C
QUESTION 219
The computers in your company’s finance department run Windows XP Professional. These computers have multiple line of business (LOB) applications installed. You add a new Windows 10 Enterprise computer in the finance department. You discover that an application used by the finance department does not work on this computer.
You need to run the application on the new computer.
What should you do first?
A. Install Client Hyper-V.
B. Run Refresh your PC.
C. Install Windows XP Mode.
D. Create a Windows To Go workspace.
Answer: A
QUESTION 220
You support Windows 10 Enterprise tablets. The tablets have the Application Virtualization (App-V) client installed.
Company policy requires that all published App-V applications be available to users only when they are connected to the company network.
You need to configure the tablets so that the company policy requirements are enforced.
What should you do?
A. Configure mandatory profiles for tablet users.
B. Reset the App-V client FileSystem cache on the tablets.
C. Disable the Disconnected operation mode on the tablets.
D. Change user permissions to the App-V applications.
Answer: C
QUESTION 221
Your company has Windows 10 Enterprise client computers.
Microsoft Application Virtualization (App-V) is used to deploy applications.
An App-V package named App1 is stored in C:\App1 on each computer.
You need to publish App1 on the computers.
Which two Windows PowerShell commands should you run? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Publish-AppVClientPackage -Name App1 -DynamicUserConfigurationPath C:\App1\config.xml
B. Add-AppVClientPackage C:\App1\config.xml
C. Add-AppVClientPackage C:\App1\App1.appv
D. Publish-AppVClientPackage -Name App1 -DynamicUserConfigurationPath C:\App1\App1.appv
Answer: AC
Explanation:
https://docs.microsoft.com/en-us/microsoft-desktop-optimization-pack/appv-v5/how-to-apply-the-user-configuration-file-by-using-powershell
QUESTION 222
Note: This question is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
You have five computers that run Windows 10. You are the only user who uses the computers. All of the computers are members of the same domain.
You need to ensure that you can access any file on any of the computers over the Internet.
What should you configure?
A. account policies
B. share permissions
C. application control policies
D. NTFS permissions
E. HomeGroup settings
F. software restriction policies
G. Encrypting File System (EFS) settings
H. Microsoft OneDrive
Answer: H
QUESTION 223
Note: This question is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details in a question apply only to that question.
You need to enable other users to establish Remote Desktop connections to your computer.
Which Control Panel application should you use?
A. Credential Manager
B. Sync Center
C. System
D. Power Options
E. Phone and Modem
F. RemoteApp and Desktop Connections
G. Network and Sharing Center
H. Work Folders
Answer: C
QUESTION 224
You have an Active Directory domain named contoso.com. Work folders are deployed.
A user named User1 has a Windows 10 Home computer that is configured to use Work Folders.
User1 connects a new removable USB drive to the computer.
User1 needs to move the Work Folders to the new drive.
What should User1 do first?
A. From the Work Folders settings, click Manage Credentials.
B. From Services, stop the Work Folders service.
C. From the Work Folders settings, click Stop using Work Folders.
D. From Services, set the BitLocker Drive Encryption Service to start automatically.
Answer: C
Explanation:
https://support.microsoft.com/en-us/help/27903/windows-10-work-folders-faq
QUESTION 225
You have an Active Directory domain named contoso.com that contains a deployment of Microsoft System Center 2012 Configuration Manager Service Pack 1 (SP1). You have a Microsoft Intune subscription that is synchronized to contoso.com by using the Microsoft Azure Active Directory Connect.
You need to ensure that you can use Configuration Manager to manage the devices that are registered to your Microsoft Intune subscription.
Which two actions should you perform? Each correct answer presents a part of the solution.
NOTE: Each correct selection is worth one point.
A. In Configuration Manager, configure the Microsoft Intune Connector role.
B. In Microsoft Intune, create a new device enrollment manager account.
C. In Configuration Manager, create the Microsoft Intune subscription.
D. In Microsoft Intune, configure an Exchange Connector.
E. Install and configure Azure Active Directory Connect.
Answer: AC
Explanation:
https://www.systemcenterdudes.com/configuring-sccm-2012-intune-integration/
QUESTION 226
You have 100 Windows computers that are managed by using Microsoft Intune.
You need to ensure that when a new critical update is released, the update is approved automatically and deployed to the computers within 24 hours of approval.
What should you do from the Microsoft Intune administration portal?
A. From the Updates node, select Critical Updates, and then modify the Approval settings.
B. From the Admin node, click Enrollment Rules, and then modify the device enrollment rules.
C. From the Admin node, click Updates, and then create a new automatic approval rule.
D. From the Policy node, click Compliance Policies, and then create a new compliance policy.
E. From the Policy node, click Configuration Policies, and then create a new Windows policy.
Answer: A
QUESTION 227
Your company has a main office and a branch office. Each office contains several servers that run Windows Server 2012.
You need to configure BranchCache for the client computers in the branch office. The solution must ensure that all of the cached content is in a central location.
What should you run on each client computer?
A. the Enable-BCDistributed cmdlet
B. the Enable-BCHostedClient cmdlet
C. the Enable-BCLocal cmdlet
D. the Enable-BCHostedServer cmdlet
Answer: D
QUESTION 228
You administer a Windows 10 Enterprise computer.
The computer is configured to encrypt several folders by using a self-signed Encrypted File System (EFS) certificate.
You need to make a backup copy of the encryption keys.
What should you do?
A. Open the Certificates console and connect to the user account certificates. Export the self-signed EFS certificate from the Trusted People folder to a Canonical Encoding Rules (CER) file.
B. Open the Certificates console and connect to the user account certificates. Find the personal self-signed EFS certificate and export it to a Personal Information Exchange (PFX) file.
C. Open the Certificates console and connect to the user account certificates. Export the personal self- signed EFS certificate from the Trusted Root Certification Authority folder to a Personal Information Exchange (PFX) file.
D. Open the Certificates console and connect to the computer account certificates. Export the self-signed EFS certificate from the Trusted People folder to a Canonical Encoding Rules(CER) file.
Answer: B
QUESTION 229
You administer Windows 10 Enterprise computers that are members of an Active Directory domain.
Some volumes on the computers are encrypted with BitLocker. The BitLocker recovery passwords are stored in Active Directory. A user forgets the BitLocker password to local drive E: and is unable to access the protected volume.
You need to provide a BitLocker recovery key to unlock the protected volume.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Ask the user for his or her logon name.
B. Ask the user for a recovery key ID for the protected drive.
C. Ask the user for his or her computer name.
D. Ask the user to run the manage-bde -protectors -disable e: command.
Answer: CD
QUESTION 230
You have a portable Windows 10 Enterprise computer.
You are creating a backup plan.
You have the following requirements:
– Automatically back up the files in your Documents folder every hour.
– Ensure that you can recover different versions of the backed-up files.
– Do not back up the Windows operating system files.
You need to configure the computer to meet the requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Connect an external hard drive to the computer.
B. Turn on File History.
C. Create a volume mount point in your Documents folder.
D. Schedule a task to create a restore point every hour.
E. Create a recovery drive on drive C.
Answer: AB
QUESTION 231
A company has Windows 10 Enterprise client computers. Finance department employees store files in the
C:\Finance directory. File History is on.
A Finance department employee attempts to restore a file to a previous version by using File History. The file is not available to restore.
You need to establish why the file history is not available and ensure that it is available in the future.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Change the File History drive.
B. Start the Volume Shadow Copy Service.
C. Move the file into a library.
D. Review the File History backup log.
Answer: CD
QUESTION 232
You administer Windows 10 Enterprise computers. You have secured the computers by using BitLocker.
You have distributed a new application to the computers. Users report that file associations for ZIP archives is broken and users are unable to open ZIP files.
You need to design a solution that recovers file association. You also need to ensure that BitLocker encryption settings are maintained.
What should you do?
A. Restore computer from the latest restore point.
B. Modify setting in Change default settings for media or devices.
C. Delete the HKEY CLASSES_ROOT\exefile\shell\open\command registry key.
D. Select Reset your PC.
Answer: A
QUESTION 233
You have a computer that runs Windows 10.
You need to ensure that the next time the computer restarts, the computer starts in safe mode.
What should you use?
A. the Restore-Computer cmdlet
B. the Bcdedit command
C. the Restart-Computer cmdlet
D. the Bootcfg command
Answer: B
70-697 dumps full version (PDF&VCE): https://www.lead2pass.com/70-697.html
Large amount of free 70-697 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDX3RYMG04cEg5aEE
You may also need:
70-698 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDa2cwaDdKY1dLdHM