2018 New Released Microsoft 70-473 Exam Dumps Free Download In Lead2pass:
https://www.lead2pass.com/70-473.html
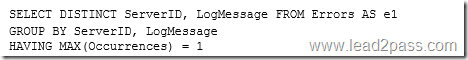
QUESTION 21
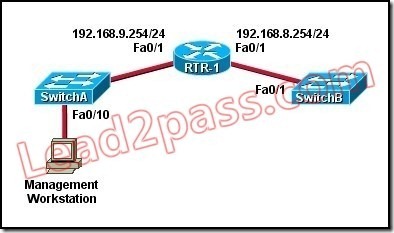
A solution for the data warehouse system must be created to provide disaster recovery between SQL03 and an Azure virtual machine named SQL04.
You need to tell the research project leaders how to migrate their databases.
Which task should you instruct the leaders to use from SQL Server Management Studio?
A. Extract Data-tier Application
B. Deploy Database to a Microsoft Azure VM
C. Deploy Database to a Microsoft Azure SQL Database
D. Copy Database
Answer: C
Explanation:
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-cloud-migrate-compatible-using-ssms-migration-wizard/
Case Study 3 – Proseware, Inc. (QUESTION 22 – QUESTION 29)
Overview
General Overview
Proseware, Inc. is a software engineering company that has 100 employees. Proseware has sales, marketing, accounts, human resources IT, and development departments.
The IT department has one team dedicated to managing the internal resources and one team dedicated to managing customer resources, which are located in the company’s hosting environment.
Proseware develops websites, basic web apps, and custom web apps. The websites and the apps are hosted and maintained in the hosting environment of Proseware.
Physical Locations
Proseware has two offices located in Seattle and Montreal. The Seattle office contains all of the hardware required to host its customers’ websites, web apps, and databases. The Seattle office contains the IT team for the hosting environment.
The Montreal office contains all of the hardware required to host the company’s internal applications, databases, and websites.
Each office connects directly to the Internet. Testing reveals that the minimum latency from the offices to Microsoft Azure is 20 ms.
Existing Environment
Internal Microsoft SQL Server Environment
Proseware uses a custom customer relationship management (CRM) application.
The internal Microsoft SQL Server environment contains two physical servers named CRM- A and CRM-B. Both servers run SQL Server 2012 Standard and host databases for the CRM application.
CRM-A hosts the principal instance and CRM-B hosts the mirrored instance of the CRM database. RM-A also hosts databases for several other applications that are used by the company’s internal applications.
CRM-A has a quad core processor and 12 GB of RAM. CRM- has a dual core processor and 8 GB of RAM.
Custom Web Applications Environment
Some Proseware customers request custom web-based applications that require more than just databases, such as SQL Server Integration Services (SSIS) and CLR stored procedures.
Proseware uses a Hyper-V server named Host1. Host1 has four instances of SQL Server 2014 Enterprise in the host operating system. The instances are mirrored on a server named Host2.
Host1 also hosts four virtual machines named VM1, VM2, VM3, and VM4. VM1 has SQL Server 2005 Standard installed. VM2 has SQL Server 2005 Enterprise Edition installed. VM3 has SQL Server 2008 Standard Edition installed. VM4 has SQL Server 2008 R2 Standard Edition installed.
Host1 uses a SAN to store all of the data and log files for the four SQL Server instances and the four virtual machines.
Websites and Basic Web Apps Environment
Proseware has two physical servers named WebServer1 and WebData1. WebServer1 hosts basic web apps and websites for its customers. WebData1 has a database for each website and each basic web app that Proseware hosts. WebData1 has four cores and 8 GB of RAM.
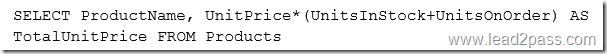
Each website database contains customer information for billing purposes. Proseware generates a consolidated report that contains data from all of these databases.
The relevant databases on WebData1 are:
– CWDB: Currently 60 GB and is not expected to exceed 100 GB. CWDB contains a table named Personallinfo.
– MovieReviewDB: Currently 5 GB and is not expected to exceed 10 GB.
Marketing Department
Proseware has a web app for the marketing department. The web app uses an Azure SQL database. Managers in the marketing department occasionally bulk load data by using a custom application. The database is updated daily.
Problem Statements
Proseware identifies the following issues:
– Lack of planning and knowledge has complicated the database environment
– Customers who have web apps hosted on Webserver1 report frequent outages caused by failures on WebDatal. The current uptime is less than 90 percent .
– Internally users complain of slow performance by the CRM application when the databases fail over to CRM-B
– WebDatal has no high availability option for the databases or the server.
– An internal licensing audit of SQL Server identifies that Proseware is non compliant. Hostl, CRM-A, and CRM-B are licensed properly. VM1 VM2, VM3, VM4, and WebDatal are unlicensed.
Requirements
Business Requirements
Proseware identifies the following business requirements:
Security Requirements
Proseware hosts a database for a company named Contoso, Ltd. Currently, all of the employees at Contoso can access all of the data in the database.
Contoso plans to limit user access to the CWDU database so that customer service representatives can see only the data from the PersonalInfo table that relates to their own customers.
QUESTION 22
You are evaluating moving the data from WebData1 to an Azure SQL database.
You need to recommend a solution to generate the consolidated report for billing.
The solution must meet the business requirements.
What should you include in the recommendation?
A. SQL Server Integration Services (SSIS)
B. SQL Server Analysis Services (SSAS)
C. an elastic database job
D. an elastic query
Answer: D
QUESTION 23
You are planning the consolidation of the databases from Host1.
You need to identify which methods to use to back up the data after the consolidation completes.
What are two possible methods that achieve this goal? Each correct answer presents a complete solution.
A. BACKUP TO URL
B. AlwaysOn failover clustering
C. a maintenance plan
D. AlwaysOn Availability Groups
Answer: AC
QUESTION 24
You need to recommend a disaster recovery solution for the CRM application that meets the business requirements.
What should you recommend?
A. backup and restore by using Windows Azure Storage
B. log shipping
C. AlwaysOn Availability Groups
D. database mirroring
Answer: A
QUESTION 25
You are evaluating whether to replace CRM-B with an Azure virtual machine.
You need to identify the required virtual machine service tier to replace CRM.
The solution must meet the following requirements:
Which virtual machine service tier should you identify?
A. Standard DS3
B. Standard A6
C. Standard GS2
D. Standard D3
Answer: A
Explanation:
https://azure.microsoft.com/en-gb/documentation/articles/virtual-machines-windows-sizes/
QUESTION 26
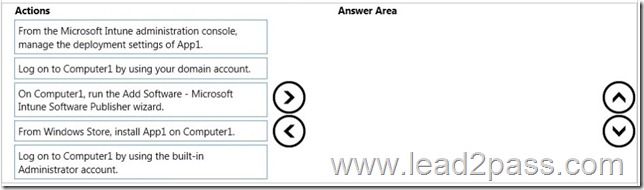
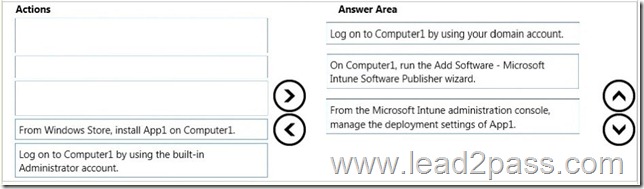
Drag and Drop Question
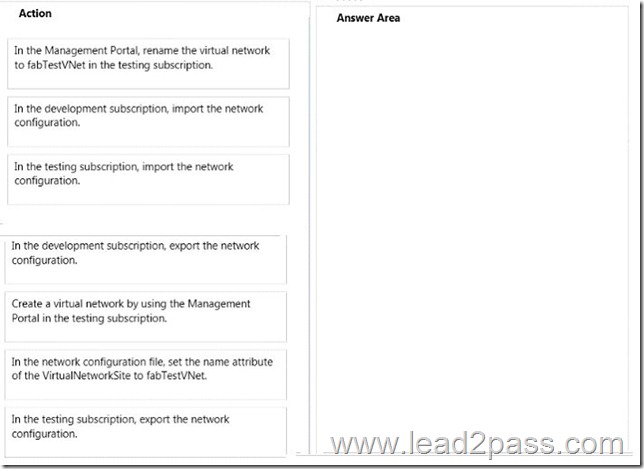
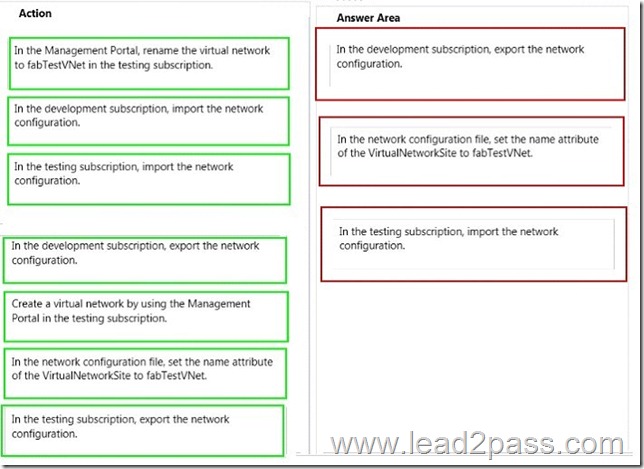
A marketing department manager reports that the marketing department database contains incorrect data. The manager reports that the data was correct yesterday.
You need to recommend a method to recover the data.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Answer: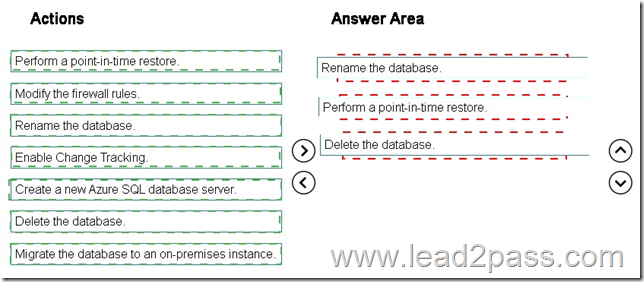
QUESTION 27
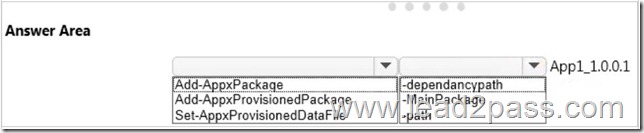
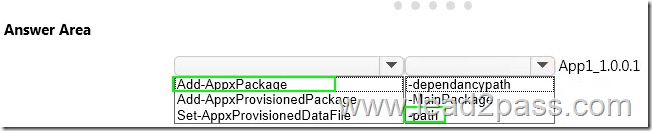
Drag and Drop Question
You plan to implement row-level security for the CWDB database.
You create the fn_limitusers function under the restriction schema.
You need to create the policy.
How should you complete the policy? To answer, drag the appropriate elements to the correct locations. Each element may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.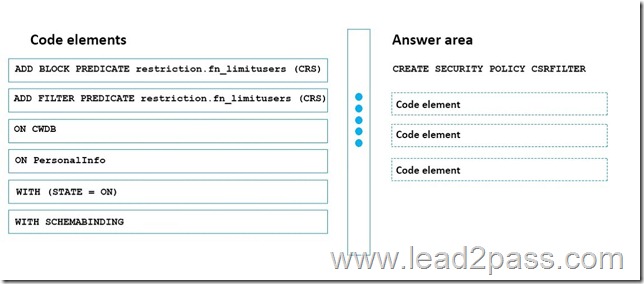
Answer: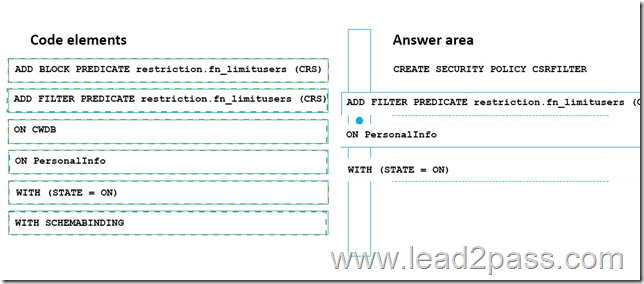
Explanation:
https://msdn.microsoft.com/en-us/library/dn765131.aspx
QUESTION 28
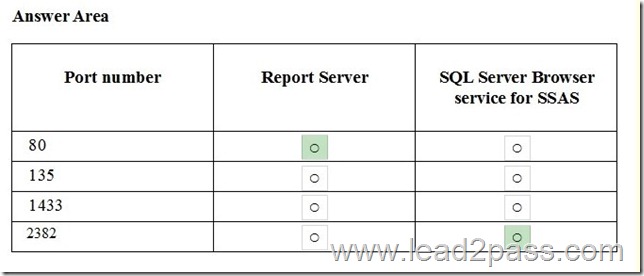
Hotspot Question
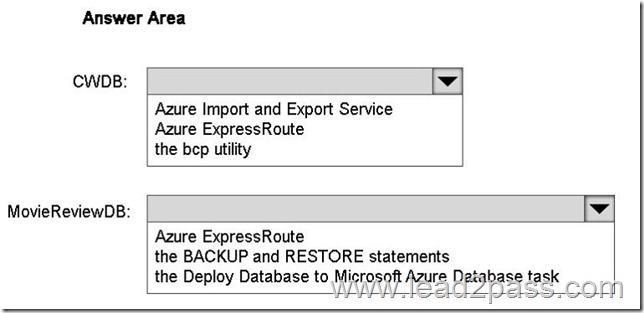
You need to identify which methods to use to migrate MovieReviewDB and CWDB.
Which method should you identify for each database? To answer, select the appropriate options in the answer area.
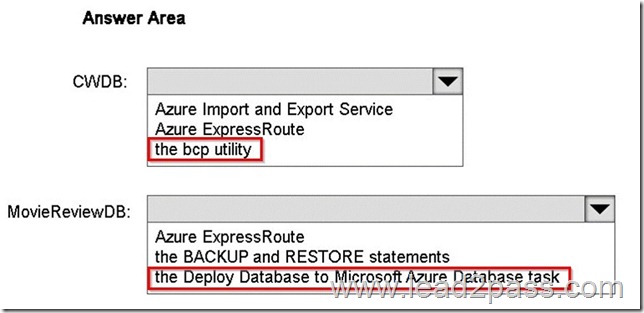
Explanation:
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-cloud-migrate-compatible-using-ssms-migration-wizard/
70-473 dumps full version (PDF&VCE): https://www.lead2pass.com/70-473.html
Large amount of free 70-473 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDTUhKaFQyeFV2QWc