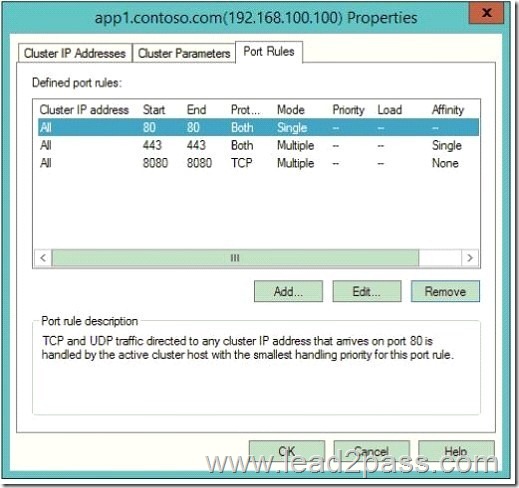
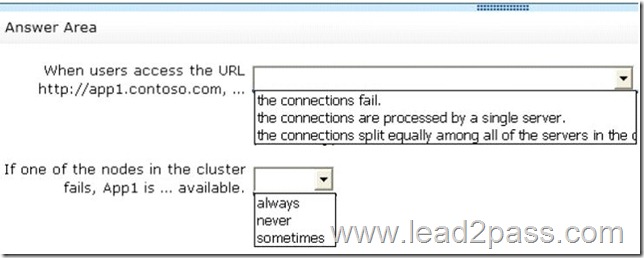
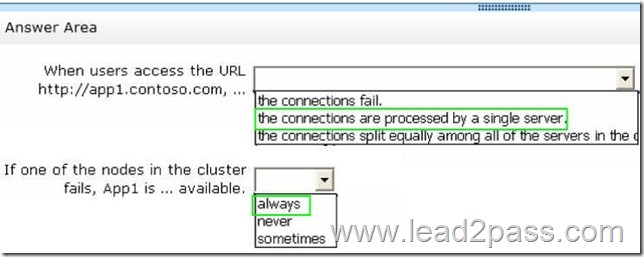
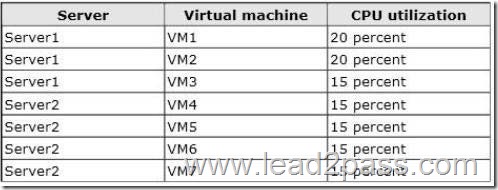
Try Lead2pass Latest PMI PMP Dumps To Pass The Exam Successfully:
https://www.lead2pass.com/pmp-exam.html
QUESTION 1
You work for a software development company that has followed the waterfall development model for more than 20 years. Lately, a number of customers have complained that your company is taking too long to complete its projects. You attended a class on agile development methods and believe that if the company used the agile approach, it could provide products to clients in a shorter time period. However, it would be a major culture change to switch from the waterfall methodology to the agile approach and to train staff members in this new approach. You mentioned this idea to the director of the PMO, and although she liked the idea, she would need approval from the company’s portfolio review board to move forward with it. She suggested that you document this idea in a______________.
A. Business need
B. Product scope description
C. Project charter
D. Business case
Answer: D
Explanation:
The business case is used to provide the necessary information to determine whether or not a project is worth its investment. It is used to justify the project and typically contains a cost-benefit analysis and a business need.
QUESTION 2
You are managing a large project with 20 key internal stakeholders, eight contractors, and six team leaders. You must devote attention to effective integrated change control. This means you are concerned primarily with______________.
A. Reviewing, approving, and controlling changes
B. Maintaining baseline integrity, integrating product and project scope, and coordinating change across knowledge areas
C. Integrating deliverables from different functional specialties on the project
D. Establishing a change control board that oversees the overall project changes
Answer: A
Explanation:
Performing integrated change control consists of coordinating and managing changes across the project. Activities that occur within the context of perform integrated change control include:
validate scope, control scope, control schedule, control costs, perform quality assurance, control
quality, manage the project team, control communications, control risks, conduct procurements, control procurements, manage stakeholder engagement, and control stakeholder engagement.
QUESTION 3
You plan to hold a series of meeting as you execute the project plan. While different attendees will attend each meeting, a best practice to follow is to:
A. Group stakeholders into categories to determine which ones should attend each meeting
B. Not mix the types of meetings on your project
C. Be sensitive to the fact that stakeholders often have very different objectives and invite them to determine the meeting’s agenda
D. Recognize that roles and responsibilities may overlap so focus on holding meetings primarily for decision making
Answer: B
Explanation:
Meetings are a tool and technique used in direct and manage project work. Meetings tend to be one of three types: information exchange; brainstorming, option evaluation, or design; or decision making. A best practice is to not combine the types of meetings and prepare for them with a well- defined agenda, purpose, objective, and time frame. They should be documented using minutes and action items.
QUESTION 4
You are the project manager in charge of developing a new shipping container for Globus Ocean Transport, which needs to withstand winds of 90 knots and swells of 30 meters. In determining the dimension of the container and the materials to be used in its fabrication, you convene a group of knowledgeable professionals to gather initial requirements, which will be included in the______________.
A. Project charter
B. Bill of materials
C. WBS
D. Project Statement of Work
Answer: A
Explanation:
The project charter documents the business needs, assumptions, constraints, understanding of the customer needs and high-level requirements and what the new product, service, or result is to satisfy. It is the document used to formally authorize the project.
QUESTION 5
You have assembled a core team to develop the project management plan for the next generation of fatigue fighting drugs. The science is complex, and the extended team of researchers, clinicians, and patients for trials exceeds 500 people. The content of your project management plan will be directed primarily by two factors. They are______________.
A. Project complexity and the capability of resources
B. Number of resources and project schedule
C. Team member experience and budget
D. Application area and complexity
Answer: D
Explanation:
The content of the project management plan is primarily influenced by the application area [in this case drug development] and complexity of the project. The size of the plan is typically commensurate with the size and complexity of the project.
QUESTION 6
When you established the change control board for your avionics project, you established specific procedures to govern its operation. The procedures require all approved changes to baselines to be reflected in the______________.
A. Performance measurement baseline
B. Change management plan
C. Quality assurance plan
D. Project management plan
Answer: D
Explanation:
The project management plan must be updated changes to subsidiary plans and baselines subject to formal change control processes. Those changes must be communicated to appropriate stakeholders in a timely manner.
QUESTION 7
You are beginning a new project staffed with a virtual team located across five countries. To help avoid conflict in work priorities among your team members and their functional managers, you ask the project sponsor to prepare a______________.
A. Memo to team members informing them that they work for you now
B. Project charter
C. Memo to the functional managers informing them that you have authority to direct their employees
D. Human resource management plan
Answer: B
Explanation:
Although the project charter cannot stop conflicts from arising, it can provide a framework to help resolve them, because it describes the project manager’s authority to apply organizational resources to project activities.
QUESTION 8
The purpose of economic value added (EVA) is to______________.
A. Determine the opportunity costs associated with the project
B. Determine a non-time-dependent measure of profit or return
C. Assess the net operating profit after taxes
D. Evaluate the return on capital percent versus the cost of capital percent
Answer: D
Explanation:
Evaluate the return on capital percent versus the cost of capital percent EVA quantifies the value a company provides to its investors and seeks to determine if a company is creating or destroying value to its shareholders. It is calculated by subtracting the expected return, (represented by the capital charge), from the actual return that a company generates, (represented by net operating profit after taxes).
QUESTION 9
Facilitation techniques are used throughout project management. Your company is embarking on a project to completely eliminate defects in its products. You are the project manager for this project, and you are developing your project charter. To assist you, which of the following facilitation techniques did you use?
A. Surveys
B. Delphi approach
C. Meeting management
D. Focus groups
Answer: C
Explanation:
Meeting management is an example of a facilitation technique used in developing the project charter as meetings may be held with key stakeholders and subject matter experts. Other facilitation techniques used to guide preparation of the charter are brainstorming, problem solving, and conflict resolution.
QUESTION 10
The direct and manage project work process truly is important in project management. It affects many other key processes and uses inputs from others. Working with your team at its kickoff meeting, you explain the key benefit of this process is to______________.
A. Implement approved changes
B. Provide overall management of the project work
C. Lead and perform activities in the project management plan
D. Perform activities to accomplish project objectives
Answer: B
Explanation:
While all of the answers apply to the direct and manage project work process, the key benefit is that it involves providing overall management of the work of the project, encompassing the other answers listed.
PMP dumps full version (PDF&VCE): https://www.lead2pass.com/pmp-exam.html
Large amount of free PMP exam questions on Google Drive: https://drive.google.com/open?id=1tWlQiea0M4b98i8adjUSdp1vjK6tanR_